What is End-to-End Encryption? How is it Different from Other Encryption?
How Encryption Works
We’ll get “end-to-end” encryption in a moment— but let’s first understand what encryption is and what it does before that.
Consciously or unconsciously, when we use the internet through our computers, we all send and receive much information. And some of this information is sensitive (passwords, financial information, personal photos, etc.) and could cause considerable harm if somebody steals or tampers with it. So, how are we to make sure nobody does that? Okay, here’s where encryption joins.
Encryption is the technique that transforms our data into an undecipherable file for no third party to be able to read or alter. That’s what keeps us safe in Internet Ocean.
Here is an example of a text sentence which was encrypted:
- Plain text: This is a Facebook message.
- Encrypted text: eXP3jH+7giCt1gIg0zHm3j3DPI1xuFRvbhmaKJx/uQQ=
As you can see, there is no way to figure out what the encrypted text implies-unless you have the private key to decrypt it, of course.
Facebook Messenger Is Already encrypted — here’s How It Works
Facebook Messenger already uses encryption — just not end-to-end encryption. “Normal” encryption (a.k.a. link encryption) works like this:
- Sender forms an encrypted connection with Facebook’s servers.
- Sender submits the encrypted message to Facebook’s servers.
- Facebook decrypts the message and stores it on their servers.
- Facebook’s servers form an encrypted connection with the recipient.
- Recipient downloads the message via an encrypted connection.
Note that in this scenario, Facebook controls the encryption/decryption, and Facebook has access to the decrypted message.
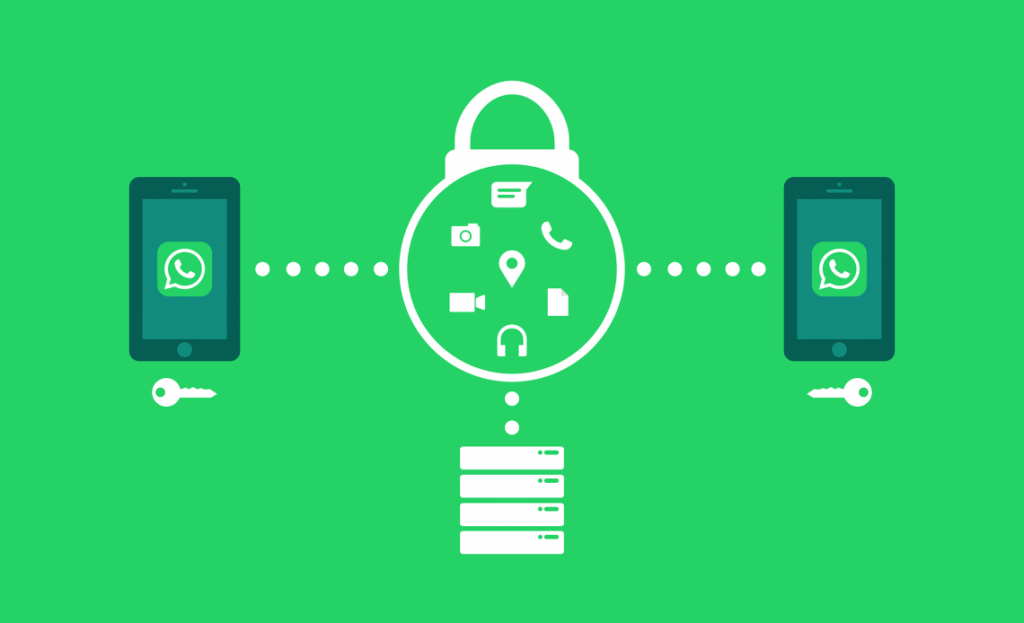
How End-to-End Encryption Works
Now, let’s get encryption end to end. It is just what it sounds like — end-to-end encryption enables the form of encrypted communication that can only be read / seen by the sender and receiver. No one in the middle — including Facebook, the government or another provider of messaging services — can read / decrypt messages from one device to another.
That is to say, the messages you send are decrypted at the contact endpoint— the computer you send messages to. The server through which you send the data (i.e. Facebook) will not be able to decrypt or display your messages.
Facebook Can’t See Your Messages When They’re End-to-End Encrypted
The distinction between the two is that while standard or link encryption encrypts the data, the encrypt data can be decrypt by the server that transmits information between two devices. On the other hand, end-to-end encryption allows the server to relay the data (how else would the data transfer take place?), but this does not require the server to decrypt the data. The server is therefore merely a medium that enables the transmission of encrypted information by data. WhatsApp or any other encrypted end-to-end app will therefore not be able to read the details (even if they so wish).
End-to-End Encryption: The Good
The principle of end-to-end encryption is largely support by security professionals and privacy experts since it better protects the data from hackers and other parties who may want to spy on you. When you authorize the data transmitter (in this case the messaging service provider) to decrypt your messages, you leave a significant potential security hole that could cause problems if the server is compromise, hack or monitor.
Nevertheless, if the information is secured end-to-end, there is no point in intercepting information halfway down the line, as it is in encrypt format. It thus preserves the privacy of millions of people and guarantees them that their private information could not be accessed by anyone— not even the messaging service itself. For this reason, experts (including organizations such as the Electronic Frontier Foundation (EFF), the Democracy & Technology Center and others) promote the use of end-to-end encryption in messaging applications.
End-to-End Encryption: The Bad
The main argument against end-to-end encryption (and for link encryption) is that end-to-end encryption creates a “safe space” for criminals to communicate where there is no third party that can read their messages and perform security checks. In other words, the technology which is suppose to protect the privacy of millions of people and businesses also protects the privacy of criminals.
I’m not saying I’m in favor of this claim but it certainly holds some weight. If the server could decrypt the data, then we could have a program that would help catch the bad guys. The option is gone in the case of end-to-end encryption. I don’t know what other motivations they might have, but that’s the justification the U.S., U.K., and Australian governments are using to up end end-to-end encryption.
End-to-End Encryption: The Politics
While the claim made by different governments may to some degree valid, there is always a question mark as to their full intent. Will they think about the crimes that may cover due to end-to-end encryption, or do they cry foul to fulfill a bigger agenda: getting the ability to spy on people easily?
Bearing in mind the evidence available to us so far, both seem likely to be true.
And it is worth noting here that Edward Snowden, the prominent whistle-blower of the National Security Agency, previously revealed the intelligence services in the U.K. And for many years the U.S. intercepted mass-scale messages via various channels. So, where are you going to draw the line as regards interference by governments? Encryption can be use for both good and bad, but surveillance can do so!
An Encryption Backdoor Is Not the Solution
If you’ve been following this whole encryption saga, you must have stumbled over the term “backdoor”. Basically, a backdoor is a mathematical feature of the encryption key exchange that could decrypt end-to-end encryption. No one knows about it except those who did it (the messaging service). It’s like a secret key in folk language. So when, let’s say, a judge orders a warrant to turn over certain information to the government in a decrypted format, the messaging app. It could use this “backdoor” to provide the government with your decrypted information.
Yet, again, this comes with a risk— a big one. What if that mighty device falls into the wrong hands? If somehow a cybercriminal gets hold of this “secret key,” they could have access to all your private pictures, texts, and so on and do who knows what about them! And that is why building a backdoor might be even more dangerous than standard encryption concerns.