How To Upgrade to Private Key Authentication
SSH is a safe way to connect to remote servers directly, but you can take a number of other steps to further ensure that your links are legitimate. The simplest and best way to do this is by using the SSH keys.
Authentication for SSH includes a public key and a private key— the public key can be freely shared on the internet, while never sharing your private key with anyone or taking it outside your local computer. You will align your private key with your public key for logging in by putting your public key on your VPS. This increases dramatically the security of the connection— SSH keys can be attacked by brute force almost impossible.
Create the SSH keys
First, create your keys on your local machine:

You’ll be prompted with a request on where to save the newly-created files.
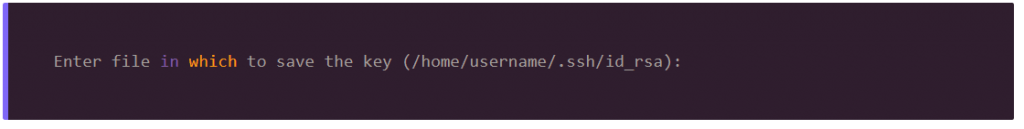
The best option here is to type Enter and place the keys in their default location. Next, you’ll be asked for a passphrase.
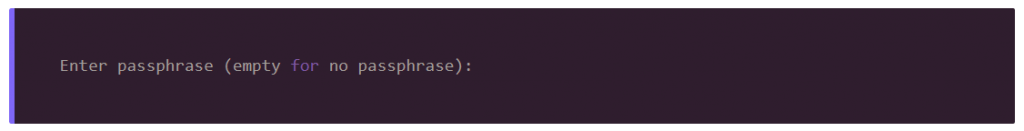
There are advantages and disadvantages of deciding whether or not you encrypt your SSH key. Passphrases offer increased security — even if a hacker gets a private passphrase, they will figure their passphrase out before they can use it. The authentication with two factor is almost like SSH.
The solid, safe passphrase ensures that every time you use your key, you are required to type it. Take into account all the variables of your application–no passphrase or weak passphrase is appropriate when this is a personal server. Security is far more critical if your server hosts user data.
You’ll ask to enter the passphrase again, no matter your choice. The program will then give some additional output, and will create your keys. The public key (the one you may share) is located at /home/local-user/.ssh/id_rsa.pub . The private key is located at /home/local-user/.ssh/id_rsa .
Copy the SSH key to your server
Now, you need to copy your public key to the VPS that you want to log into. The easiest way to do this is to use the ssh-copy-id program.

If you don’t have that program available, you can also use the following command, which pipes the content of your public key file through SSH and appends the output to the end of the authorized_keys file on your server.
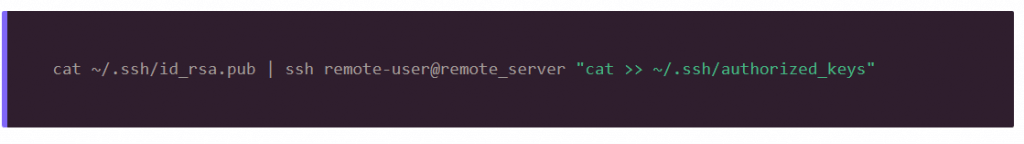
You’ll see some output related to connecting to the server and copying your public key into the authorized_keys file on the VPS. Now you can try logging in with SSH again.

You will be sign in automatically if you did not secure your SSH key with a passphrase. SSH will order it if you use the passphrase. It’s important to remember that SSH needs a Passphrase for your SSH username, not one of your previous user passwords.
Disable password-based logins
You can improve safety by de-activating password-based logins for root users and others once you have ensured that you can log into your VPS using SSH keys.
Log into your VPS if you’re not already.

Open up the SSH configuration file in your editor of choice. nano is a user-friendly option for those newer to Linux administration.

You’re looking for two lines: one that begins with PermitRootLogin and another that begins with PasswordAuthentication . Change them to the following:

Finally, reload ssh to enable this change (for Ubuntu-based servers).

Now you will be able to log into your future root account using your SSH key. You cannot log into the root account directly.